
Vulnerability Management for everyone: Why Per-Device Scanning Doesn’t Have to Break the Bank
In today’s increasingly hostile digital landscape, vulnerability management isn’t just for the big players anymore. Small and medium-sized businesses (SMBs) are rapidly recognizing this reality— with an increased threat surface from ransomware and phishing attacks targeting key areas of smaller businesses, who might not have the culture or tooling to protect themselves the same as larger or enterprise organisations.
So here’s the challenge: while the market offers numerous vulnerability management solutions (Enough tools to make you dizzy with ‘choice’), many come with enterprise-level price tags that just don’t make sense for even the most security-conscious small business owner. When you’re looking at figures like £3,590 per year for a single Tenable Nessus Professional license or Qualys starting at £199 per asset annually, the math quickly becomes discouraging for growing businesses. Solopreneurs or consultants equally might think that this is out of reach for them too.
The good news? There’s a way to make comprehensive vulnerability management much more affordable—without sacrificing quality (Spoilers, we’re offering it). Let’s dive into why per-device scanning matters and how smaller organizations can access enterprise-grade security at small business prices.
Why Endpoint Scanning Matters in an IAM-Focused Security World
Identity and Access Management (IAM) has dominated security conversations in recent years—and for good reason. Managing who can access what remains critical to security. But focusing solely on identity while neglecting the devices themselves creates a dangerous blind spot.
IAM (Identity and Access Management) is a security approach that controls who can access specific computer systems, applications, and data by managing user identities and their permissions. It ensures that people and systems only have access to exactly what they need and nothing more. In a lot of organisations, this is achieved by using Microsoft licenses attached to emails which are then given permission to files or locations.
Here’s why endpoint scanning remains essential:
- The attack surface has exploded: With remote work now standard, company assets access sensitive resources from countless locations and networks.
- Unpatched devices are prime targets: Attackers don’t need sophisticated techniques when they can exploit known vulnerabilities that simply haven’t been patched.
- Configuration drift happens: Even with strict policies, devices drift from secure configurations over time—and you can’t fix what you can’t see.
- “Zero Trust” isn’t zero without device health: True Zero Trust architecture requires verification of device security posture before granting access to resources.
- Manged Service Providers or IT don’t always have structures of accountability that incentivize keeping your network as patched and up to scratch as you think it is.
Whether you’re a team of 1 or 100, making sure the device you work on is secure really is step 1. This often gets lost in the focus on controlling access to accounts and securing identity with MFA and Password Managers (Equally as important!). Device security often gets reduced to having an anti-virus and keeping your device up to date, this is good – but it’s not enough.
Beyond Patching: The Reality of Vulnerability Management
So effective vulnerability management isn’t just about keeping software up to date, though that’s certainly part of it. The full picture encompasses:
Software Inventory and Assessment
Before you can secure your environment, you need to know exactly what’s running in it. Good quality vulnerability management gives you comprehensive visibility into:
- Installed applications with issues, and their versions
- Outdated or unsupported software
- Shadow IT that may have slipped past procurement
Configuration Management
Many breaches exploit not missing patches, but misconfiguration that sit on any PC (Even a PC that is apparently ‘up to date’):
- Unnecessary services
- Default credentials or settings
- Settings that require a certain configuration
- Disabled security features
Practical Remediation in Imperfect Environments
Speaking candidly —no business environment is perfect, especially in growing or rapidly maturing organizations. As consultants we see this all the time, even when organisations are making strong concerted efforts to improve and have that top level buy-in, the per-device controls simply aren’t present. Quality vulnerability management accounts for the real-world constraints that are proper to being a living, breathing business:
- Prioritizing fixes based on actual risk (not just CVSS scores)
- Offering mitigation options when immediate patching isn’t feasible
- Working around legacy systems and business-critical applications
- Balancing security needs with operational requirements
This is where the “management” in vulnerability management really matters. It’s not just finding problems—it’s helping you solve them pragmatically. This can be a real limit of tool-focused approaches; even if you’re generating the information, how do you make it actionable and useful in your exact context?
Breaking the Cost Barrier: A Small Business-Friendly Approach
Here’s where we’ve got some genuinely good news. At ADAS, we’ve developed a vulnerability management approach specifically designed for small and growing businesses—one that dramatically reduces the cost per endpoint while maintaining enterprise-level capabilities. We’re proud of the approach, and it has only been made possible by the understanding of the SME landscape cultivated by our teams years in the not-for-profit and public sector space. We’ve got a really solid offering here that scales with you and invites organizations of all shapes and size into the tent.
How low can it go? Our model brings the cost down to approximately 25p per agent per month for smaller organizations—a fraction of the typical market rates we’ve seen in the research (remember those £199 per asset annual fees? Makes them look a bit silly now).
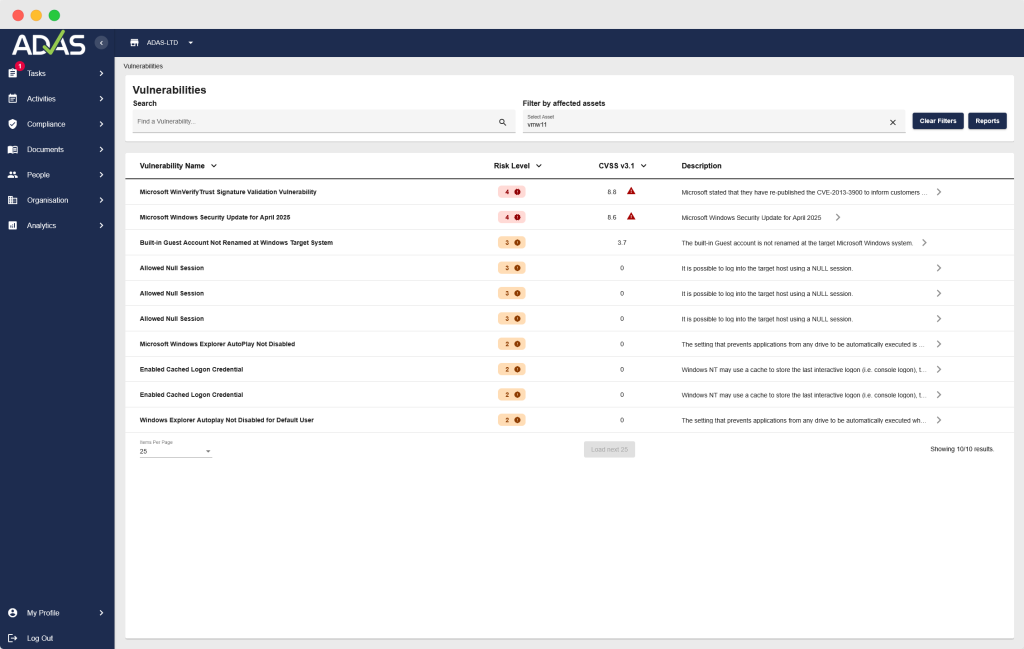
Here’s a look at an example dashboard of daily scans (Filtered for one Windows device). Users can pull reports in PDF or CSV form (Absolutely great for Power BI dashboards), and each issue comes with a suggested remediation.
Our Small Business-Friendly Model
For organizations with fewer than 50 devices:
- £10 monthly subscription
- Just £1 per standard user for dashboard access
- Self-service scanning capabilities to build in-house expertise
- Flexible hourly support rates—only pay for expert help when you need it, with prepaid blocks of hours available for use at your convenience and time scale.
For growing businesses with 50+ devices:
- Only 50p per asset per month
- No administrative fees or base subscription costs
- Enterprise-grade scanning and reporting
We’re operating this model at cost – and we only make money on support and consultancy. We decided early on that for the most part this is a mission-focused provision, and that everyone who wants access to straight forward vulnerability management should be able to get it!
Why This Approach Works for SMBs
This model is designed to address the specific challenges smaller organizations face:
- Predictable, manageable costs: No surprise bills or complex licensing structures
- Flexibility to grow: Scale up gradually without massive jumps in expense
- Building internal capability: Self-service options mean your team learns while doing – The concept of continuous improvement for human resources is often overlooked by tooling
- Expert help on demand: Get consulting support precisely when needed, without ongoing overhead
Practical Recommendations for Implementation
Regardless of whether you’re interested in “The ADAS Approach”, here are key considerations for implementing vulnerability management in your organization:
1. Start with Critical Assets
Don’t try to boil the ocean. Begin with your most business-critical systems:
- Public-facing applications and infrastructure
- Systems handling sensitive customer data
- Critical operational technology
2. Establish Your Baseline
Before making improvements, understand your current state:
- Run initial comprehensive scans
- Document your “normal” to identify anomalies later
- Take effort to understand ‘risk’ in the context of your own risk appetite, not the tooling that you’re using. Some risks are bigger than the tooling presents, others are barely something to worry about – it all depends on context!
3. Define Clear Remediation Pathways
Create practical processes for addressing findings:
- Who receives reports?
- How are vulnerabilities prioritized?
- If you use an IT provider or any third party support – do you have an SLA for remediation?
- How are exceptions handled (It’s absolutely vital to have a process for when something new blindsides you! Otherwise these things end up down the back of the sofa, put off for another day that never comes)
4. Integrate with Broader Security Efforts
Vulnerability management doesn’t exist in isolation:
- Feed findings into your risk management processes and integrate this into your broader risk assessments
- Link to incident response planning and business continuity plans
- If you’re a smaller team, find a leader to get stuck in with the terms of reference and key concepts at play; this is a priceless investment that will help the entire organization navigate cyber security for years to come.
5. Leverage for Compliance Requirements
A robust vulnerability management program simplifies meeting various compliance requirements:
For ISO 27001:
- Supports various control requirements across the standard, and is a great piece of evidence for auditors (Provided it’s properly integrated into your wider management system!)
- Provides evidence for continuous monitoring and improvement
- Demonstrates due diligence in security operations
For Cyber Essentials Plus:
- Our offered approach is approved as an IASME Cyber Essentials vulnerability scanner, so every scan is a step towards a pass for Cyber Essentials Plus!
- Self-service scanning and reporting means you can get ready for your assessment months ahead of schedule, and only leverage consultancy or expensive support when you absolutely need to.
Conclusion: Security That Scales With Your Business
Vulnerability management doesn’t need to be a luxury—it’s a fundamental security control that businesses of all sizes need. But that doesn’t mean small businesses should pay enterprise prices or settle for inadequate tooling that doesn’t connect with your strategic goals or priorities.
By adopting a flexible, service-focused approach to vulnerability management, organizations can:
- Start small with appropriate investments that protect core assets and infrastructure
- Build internal capability systematically and over a timescale that suits them
- Access expert guidance when needed
- Scale security at the rate of business growth
At ADAS Ltd, we believe security fundamentals should be accessible to everyone. Our vulnerability management service delivers enterprise-grade security with small business sensibility—proving you don’t need a Fortune 500 budget to protect your business like one.
Ready to explore how affordable, effective vulnerability management could work for your team? Get in touch today for a no-obligation chat about the best approach to vulnerability management (We don’t have a sales team, so you’ll be talking directly with the consultant who would support you – an added bonus of working with a small business).

